A Well Done Phishing Attempt
Today I received this fairly well done phishing attempt about a “2017 Outlook Web Access” migration. The landing page presents a OWA login screen like this:
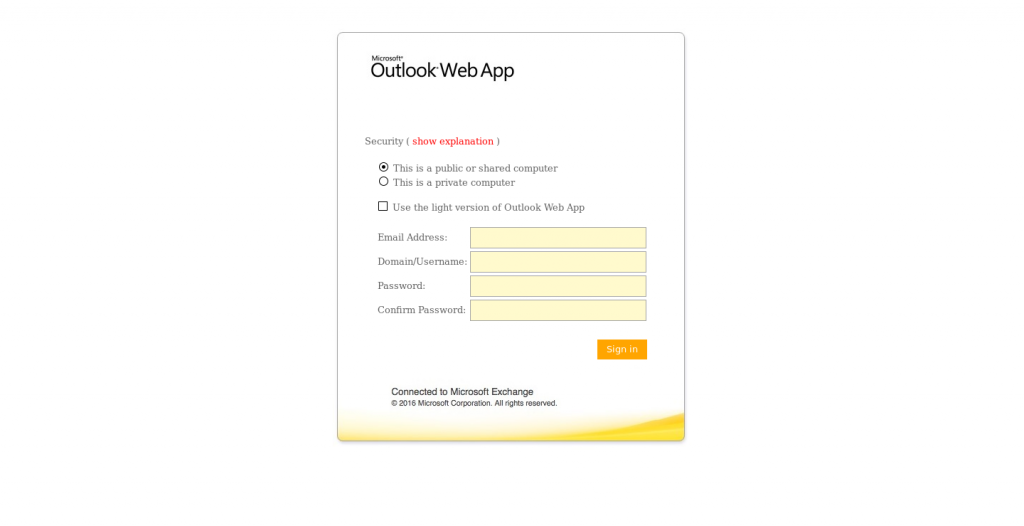
The body of the email uses some somewhat convincing language to try to get the recipient to feel a sense of urgency, panic, or anxiety. It is signed by the generic “Admin Help Desk”. I used to work in a shop that had an Admin Helpdesk and a Health Center Helpdesk, so that’s a realistic claim.
Attention E-mail User
If you are a faculty or staff member who has not yet had their email migrated to the present Web-Mail to create space for 2017 Outlook Web Access which has a high visual definition and creates more space and easy access to e-mail, Please kindly update your account by clicking on the link below and fill information for activation.
MIGRATE NOW (link to hxxp://makeiwo.cf/js/outlook)
Follow the procedure and complete information by clicking SIGN IN. A new space will be created within 48 hours. Failure to update your Web-Mail we will deactivate such accounts as it will be considered inactive.
Thank You
Admin Help Desk
How Did it Get Through?
It seems like this phishing attempt actually originated from a compromised Office 365 account, and that helped it to make it through some spam filtering, all thought the x-originating-ip shows 61.6.72.106, which it turns out is an address in Malaysia. This snip shows the first hop from the client in the headers.
Received: from CY4PR11MB1621.namprd11.prod.outlook.com ([10.172.71.9]) by CY4PR11MB1621.namprd11.prod.outlook.com ([10.172.71.9]) with mapi id 15.01.1240.020; Mon, 10 Jul 2017 18:50:29 +0000 From: Nancy Simon <nsimon@palihigh.org> To: "man@alsea.k12.or.us" <man@alsea.k12.or.us> Subject: Attention E-mail User Thread-Topic: Attention E-mail User Thread-Index: AQHS+a1hNFfSNUlFT0W/DnUrqapvqg== Date: Mon, 10 Jul 2017 18:50:29 +0000 Message-ID: <CY4PR11MB1621D53137A7BCF015F89B90ACA90@CY4PR11MB1621.namprd11.prod.outlook.com> Accept-Language: en-US Content-Language: en-US X-MS-Has-Attach: X-MS-TNEF-Correlator: authentication-results: alsea.k12.or.us; dkim=none (message not signed) header.d=none;alsea.k12.or.us; dmarc=none action=none header.from=palihigh.org; x-originating-ip: [61.6.72.106]
It has a nice, attention grabbing subject, “Attention E-mail User”. That’s going to be pretty on-target for anyone who receives this. One giveaway on the fake login page is that the layout is from a 2007 or 2010 install of Exchange. The format was update in subsequent versions, but that may not be something that is easily spotted by someone who doesn’t work with Exchange servers often.
Wikipedia puts the town of Alsea, OR at a population of 164, and Pacific Palisades, CA outside of Los Angeles boasts about 27,000 residents, and the 1976 film Carrie was filmed at Palisades High School. A web search shows Nancy Simon in attendance via various meeting minutes for the school, and other email addresses in the documents match the naming convention of first initial and last name.
The Take Away
Probably the biggest take away with this event is to reinforce employee training and communication. Training and communication from the Security team, or IT team if there isn’t anyone dedicated to security, to the rest of the organization is important. It is important to keep a regular cadence of both so that employees are aware of different scenarios, and have more exposure to a variety these types of phishing attacks without becoming victims. Regular communication is important as well. Communicate changes clearly and regularly so that some red flags go up when a change comes up that hasn’t been communicated. We want people to say “Hmmm, I always get notified about any big changes in IT, and there wasn’t any notification about this one. Maybe I should check with someone.” Another tip that can be useful is to try to brand those communications so that the recipients get used to what they look like. This helps them spot fake communications that aren’t branded.
On the more technical side, there are several mitigating controls that may help. First, possibly a web content filtering solution. Some may be able to detect a password field being sent to a clear text web page. As of this writing, Virustotal and Checkpoint both saw the URL as unknown/uncategorized. A CASB solution hooked into Office365 may have seen the email as spammy as it was making it through the Outlook.com servers. Finally, one of my favorite controls for the price is multi-factor authentication. The password may have gotten away, but if the username/password combo alone won’t let the attacker in without an additional form of authentication, I’d call that close to a win.